ASSESSING YOUR ORGANIZATION’S CYBER SECURITY: THINK YOU’RE UP TO IT?
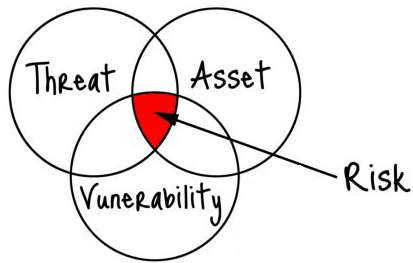
The Enron debacle will forevermore be a parable about delusional self-auditing. In much the same way, Cyber Security should never be assessed using internal staff and mechanisms, the ramifications of missing something are simply too great.
According to Cenzic ‘s Application Vulnerability Trends Report: 2014, “While the majority of corporations have the important security building blocks, such as firewalls and intrusion protection systems needed for their security infrastructure, not enough organizations have comprehensive tools and practices in place for securing applications.” Faced with a worldwide shortage of Cyber Security professionals (Cyber Security has only recently become a discipline one may major in!), and companies unable to afford the overhead necessary for the requisite training, this situation is not surprising. Bad news for you. Good news for hackers.
Still think you can go it alone? Do you really understand the sheer magnitude of possible vulnerabilities? Here’s a sobering thought: Everything on the network is hackable. Everything—from your corporate computers to a 3rd party vendor to your employees’ Smartphones. Add to this the risky behaviors employees can engage in—sharing passwords, inappropriate web browsing, copying sensitive data onto mobile devices—and you’ve got exposure. Lots of it.
An objective Cyber Security assessment can assist with evaluation and establishment of controls to:
Implement an information risk management program
Ensure network security is adequate, including boundary and internal
Guide user education and awareness
Verify malware protection and prevention
Deal with secure configuration and patch management for devices (network, servers, PCs)
Manage user access and privileges
Handle incident management
Assist with home and mobile working
If you feel you aren’t ready to tackle all the items above, you should at least undertake a basic evaluation to consider only the most foundational building blocks for cyber security.
In a survey of its 3,400 global members, …
[ Read More ]