Are you too focused on the technical aspects of cyber security?
When someone mentions information security, invariably thoughts go to technical aspects such as firewalls, routers, wireless access points and how to set those devices up—or to physical aspects such as locks, security guards and fences. These are the technical and physical controls that usually comprise our understanding of how to achieve the best level of security possible. But controls for information security fall into three main categories: the physical and technical—which we’ve already described—and the administrative, which often receives short shrift. Why?
My guess is that administrative controls are considered “soft,” focusing on management and training, and it’s pretty enticing to think that technical controls and physical controls will suffice for cyber security defense. Not a good idea, says Art Gilliland, senior vice president and general manager for Hewlett-Packard’s software enterprise security products in a recent issue of Computer World.
“…businesses and government agencies often focus on the next “silver bullet” product, unaware that most cybersecurity problems stem from flawed procedures and human error…invest in your people and process.”
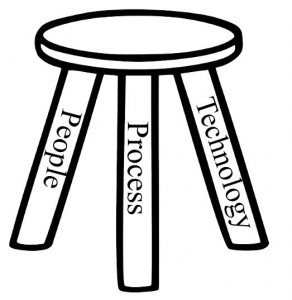
In the broader world of business, success depends on the correct balance of the three main pillars: people, process, and technology. Within information security, are we creating a three-legged stool with one leg (technology) longer than the others? That can’t be good. Technology is an important piece of your arsenal, but insufficient by itself. Having sound policies, defining clear role-based processes and procedures, and providing communications and training for key stakeholders (which may include every employee) will create balance for the three-legged stool of information security. Policies and processes might sound like management overhead, but any organization desiring to provide consistent goods and services must have consistently applied policies and processes—i.e., CMMI, but that’s a topic for another …
[ Read More ]